What is Network?
In simple term, It's just mean a computer connected to communicate
What is the Internet?
Internet is a collection of this Computer Network
Networking Fundamentals:
World Wide Web (WWW):
World Wide Web is the collection of pages of information, known as web pages, that can be accessed on the Internet. It is called a web because all the web pages are linked.
Examples:- google.com, amazon.com.
Client-Server Architecture:
Client: When we talk about the word Client, it means to talk to a person or an organization using a particular service. Similarly in the digital world, a Client is a computer (Host) i.e. capable of receiving information or using a particular service from the service providers (Servers).
Servers: Similarly, when we talk about the word Servers, It means a person or medium that serves something. Similarly in this digital world, a Server is a remote computer that provides information (data) or access to particular services.
When the client computer sends a request for data to the server through the internet, the server accepts the requested process and delivers the data packets requested back to the client.

Protocol:
A protocol is a set of rules and guidelines for communicating data. Rules are defined for each step and process during communication between two or more computers
Examples:- TCP, UDP, HTTP, HTTPS, DNS, FTP, SMTP, etc.
TCP:- Transmission Control Protocol
It will ensure that the data will reach its destination and not get corrupted on the way. It is a connection-oriented protocol, meaning that it establishes a connection between applications before transmitting any data.
UDP:- User Datagram Protocol
When you don't care whether the data has been sent to your friend or anyone else. it may change and may not be in order. It is a protocol that does not establish a connection and provides a basic but not dependable message service. It does not offer any mechanisms for flow control, error recovery, or reliability.
Ex. Video streaming (Zoom, Video call), Gaming.
HTTP:- Hyper Text Transfer Protocol
It is a stateless protocol, a client-server protocol that tells us how to request this data from the server and also how the server sent back data to the client
Ex. Web Browser(google.com, Microsoft.com)
FTP:- File Transfer Protocol
File Transfer Protocol (FTP) is a standard network protocol used for transferring files between a client and a server on a computer network. It is commonly used for uploading and downloading files from a remote server. Here are some key aspects of FTP
SMTP:- Simple Mail Transfer Protocol
It is a communication protocol used for sending and receiving email messages between servers. SMTP is responsible for the transmission of outgoing emails from a mail client or application to a mail server, as well as the relay of incoming emails between mail servers.
POP3:- Post Office Protocol
It is a standard email retrieval protocol widely used for downloading email messages from a mail server to a client device. It is one of the most common protocols for email retrieval along with IMAP (Internet Message Access Protocol).
SSH:- Secure Shell
It is a network protocol that allows secure remote access and control of a computer over an unsecured network. It provides a secure channel over an insecure network by using encryption and authentication methods.
Telnet:-
TELNET is a protocol that provides a command line interface for communication with a remote device or server, sometimes employed for remote management but also for initial device setup like network hardware.
IP Address:-
Every single device on the Internet that can talk to each other for that they have an IP address. IP addresses are used to identify devices and are unique to a device within a subnet.
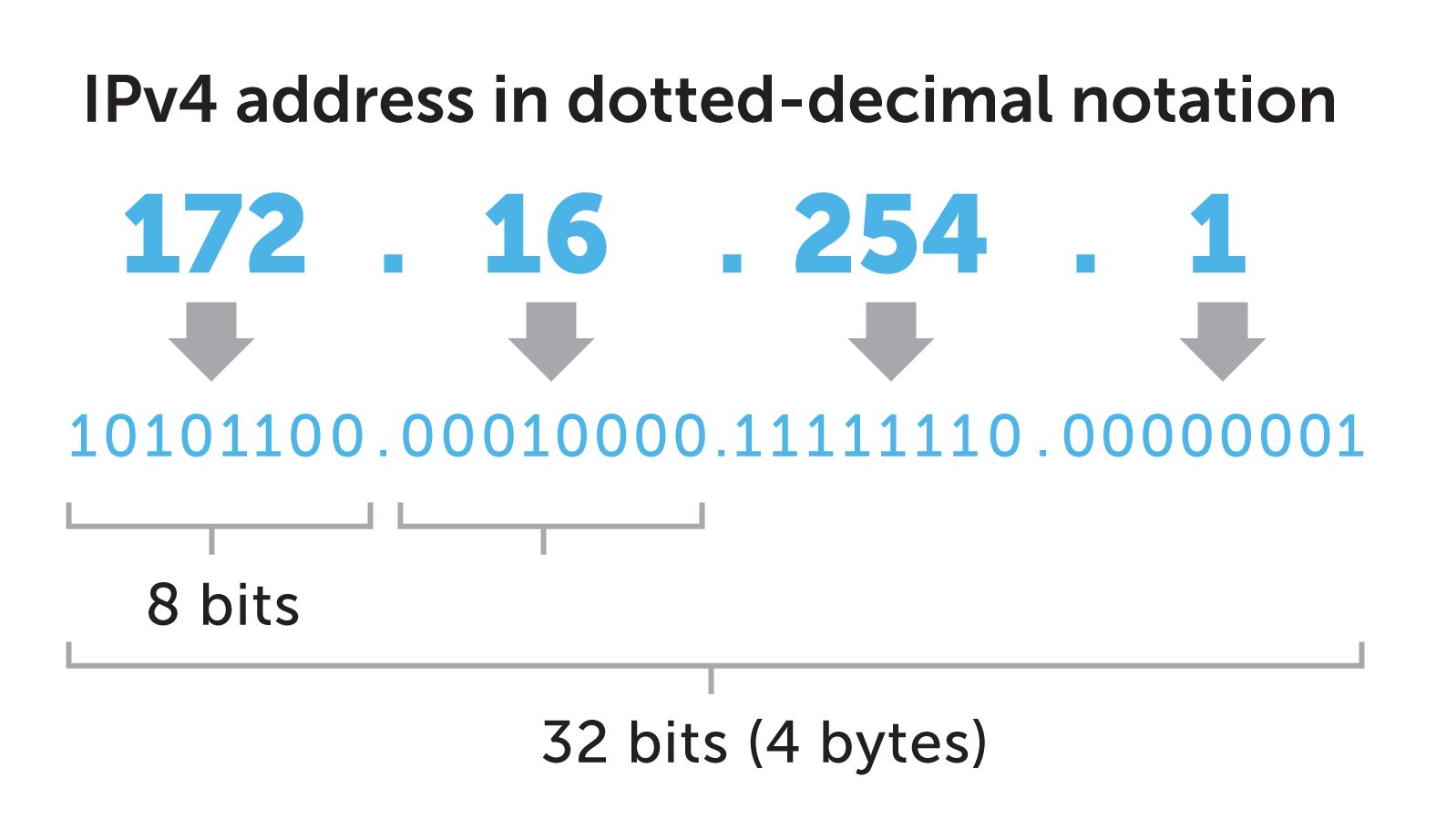
Each number in the set can range from 0 to 255. So, the full IP addressing range goes from 0.0.0.0 to 255.255.255.255. Assigned by DHCP(Dynamic Host Configuration Protocol) through the router of any ISP(Internet Service Provider)
Subnet:-
A subnet is a smaller network within a larger network that is created by dividing an IP network into multiple smaller subnetworks.
Subnet Mask:-
A subnet mask is a 32-bit number used to identify which part of an IP address represents the network portion and which part represents the host portion.


OSI and TCP/IP Model:-
OSI (Open Systems Interconnection) is a conceptual model that describes how data is transmitted and received over a network. It was developed by the International Organization for Standardization (ISO) to promote standardization in communication protocols.
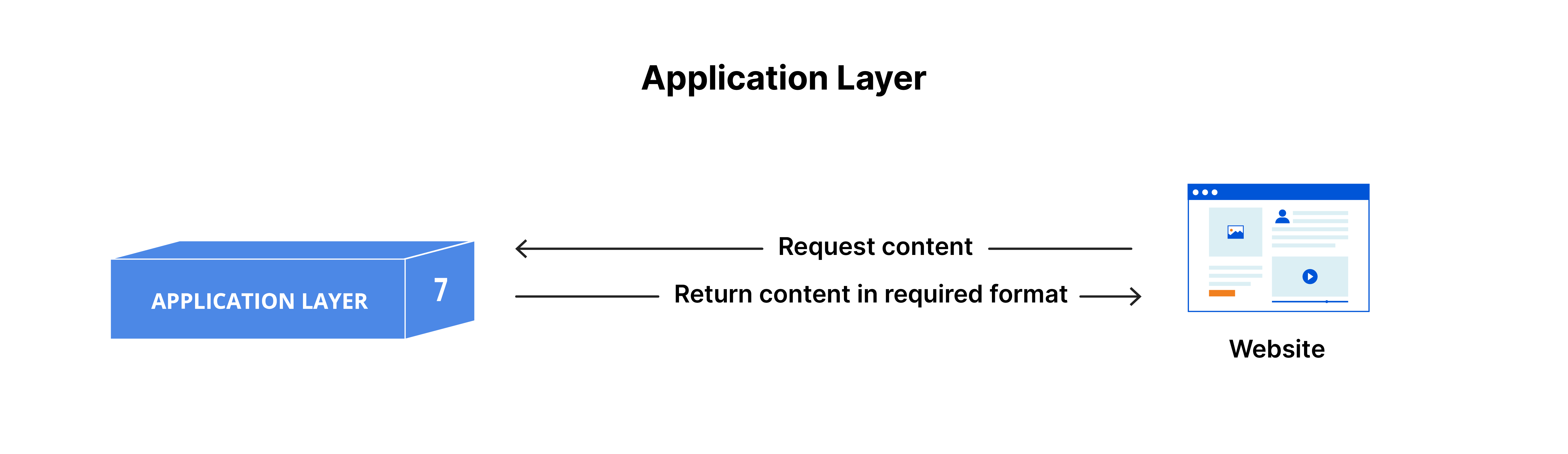
Application Layer:-
This is the only layer that directly interacts with data from the user. Software applications like web browsers and email clients rely on the application layer to initiate
Application layer protocols include HTTP, HTTPS as well as SMTP.
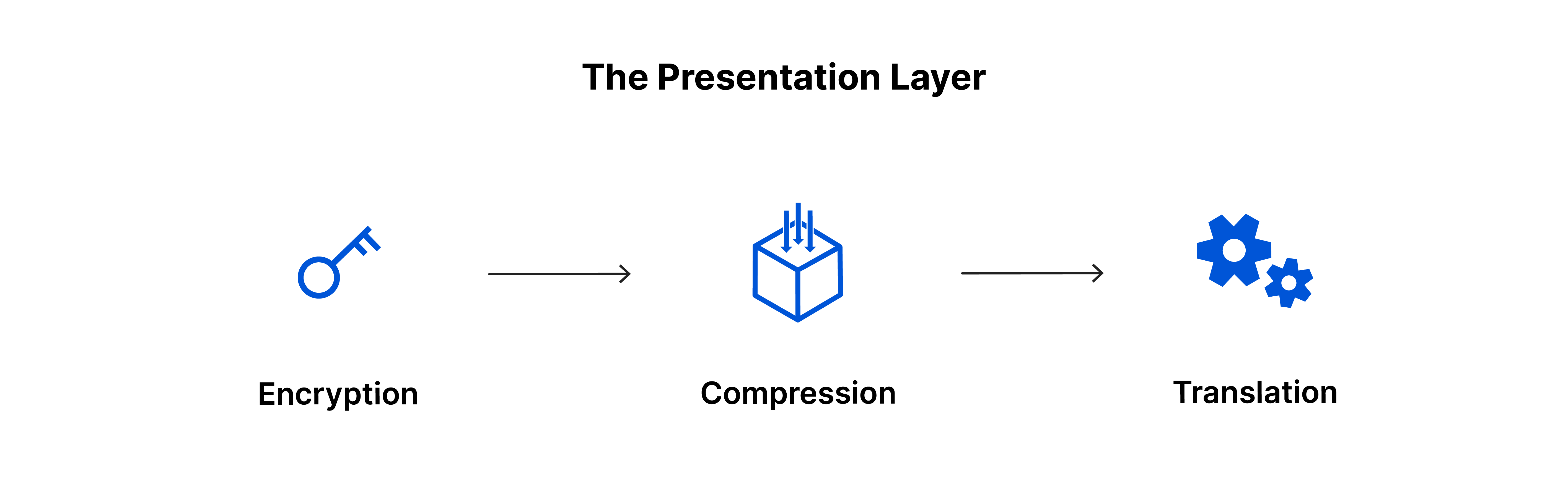
Presentation Layer:-
The presentation layer makes the data presentable for applications to consume. The presentation layer is responsible for the translation, encryption, and compression of data.
The presentation layer, or layer 6 of the OSI model, plays a crucial role in ensuring seamless communication between two devices that may be using different encoding methods. It translates incoming data into a syntax that can be understood by the application layer of the receiving device and adds encryption on the sender's end while decoding it on the receiver's end.
In addition, the presentation layer compresses data it receives from the application layer before delivering it to layer 5. This helps to optimize the speed and efficiency of communication by reducing the amount of data that needs to be transferred.
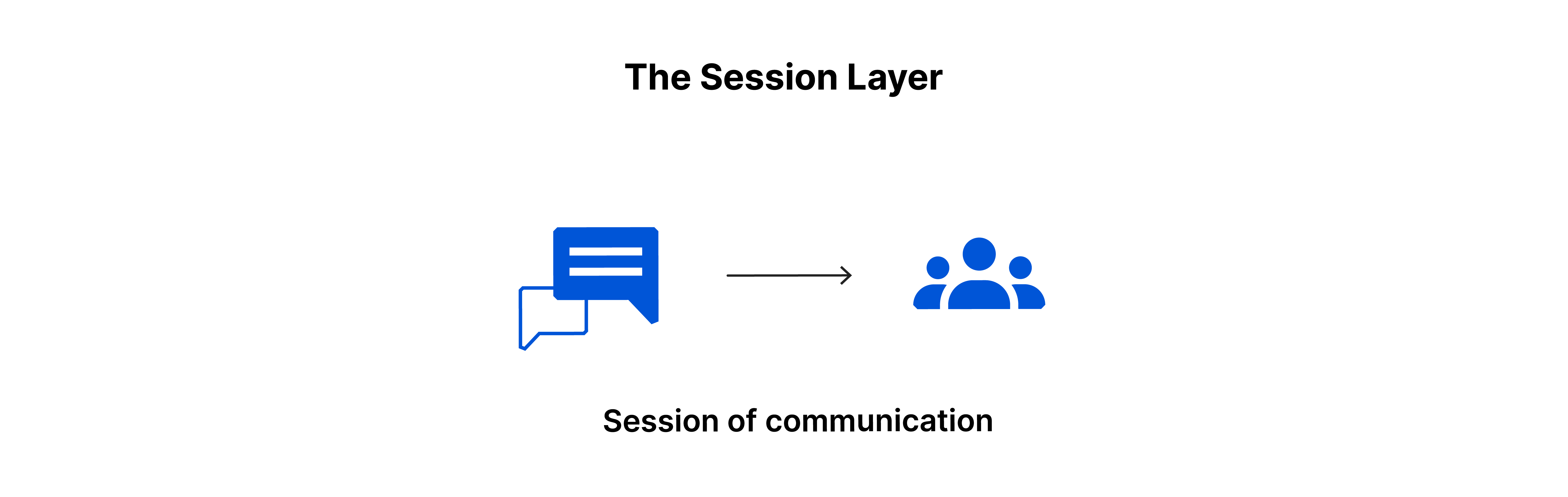
Session Layer:-
The layer that manages the opening and closing of communication between two devices is known as the session layer. It ensures that the session remains open for the duration of the data transfer, and then closes it promptly to conserve resources.
Additionally, it synchronizes data transfer with checkpoints. For example, if a 100-megabyte file is being transferred, the session layer could set a checkpoint every 5 megabytes. In the case of a disconnect or a crash, after 52 megabytes have been transferred, the session could be resumed from the last checkpoint, meaning only 50 more megabytes of data need to be transferred. Without the checkpoints, the entire transfer would have to begin again from scratch.
Transport Layer:-
The transport layer lies Inside The devices and the role of the layer is to take the information of the sender from the network to the application. Within that computer transportation of data from the network to the application is done by the transport layer
This includes taking data from the session layer and breaking it up into chunks called segments before sending it to layer 3.
When the msg is received on this computer which application do I send this msg to like WhatApp, google, etc that is done by the transport layer.
Transport layer protocols include the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
Network layer:-
From one PC to another PC the transportation part is done by the Network layer.
The network layer is responsible for enabling data transfer between distinct networks. It is not needed if the communicating devices are on the same network. The network layer divides segments from the transport layer into smaller units known as packets on the sender's device and then reassembles these packets on the receiving device. Additionally, the network layer determines the most efficient physical path for the data to reach its destination, which is referred to as routing. IP, ICMP, IGMP, and IPsec suite are among the network layer protocols.
Data-Link Layer:-
The data link layer is similar to the network layer, but it manages data transfer between two devices on the same network. The data link layer divides packets from the network layer into smaller units known as frames. also assigned mac address It is also responsible for flow control and error control in intra-network communication, like the network layer.
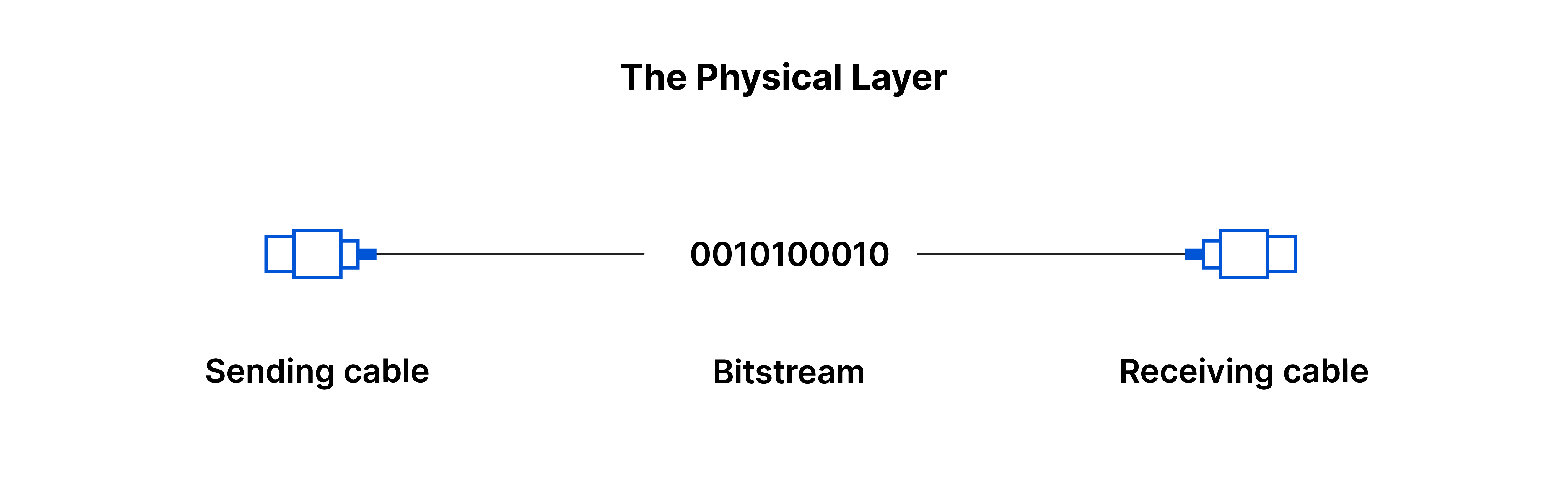
Physical Layer:-
The physical layer consists of the hardware used for data transfer, including cables and switches. Here, data is transformed into a bit stream, which is a sequence of 1s and 0s. Additionally, the physical layer requires both devices to agree on a signal convention to differentiate between 1s and 0s.

Topologies
Topology in networking refers to how devices and connections are organized in a network, either physically or logically. There are various types of network topologies,
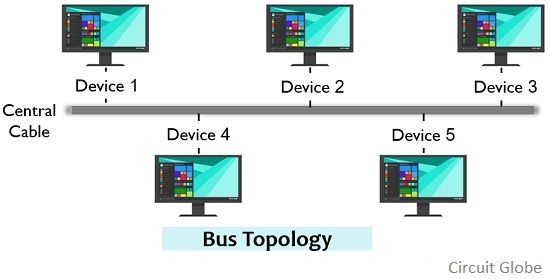
- Bus Topology: A bus topology involves connecting all devices to a single communication line known as a bus. This means that all devices share the same communication medium and data is transmitted in two directions. However, if the bus becomes overloaded or fails, the entire network may suffer adverse effects.
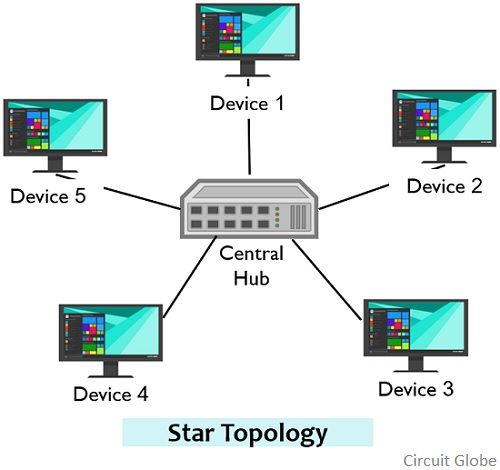
- Star Topology: In a star topology, all devices are connected to a central device, such as a switch or hub. Each device has its own dedicated connection to the central device, forming a star-like structure. If one device fails, it does not affect the rest of the network. However, the central device can become a single point of failure.
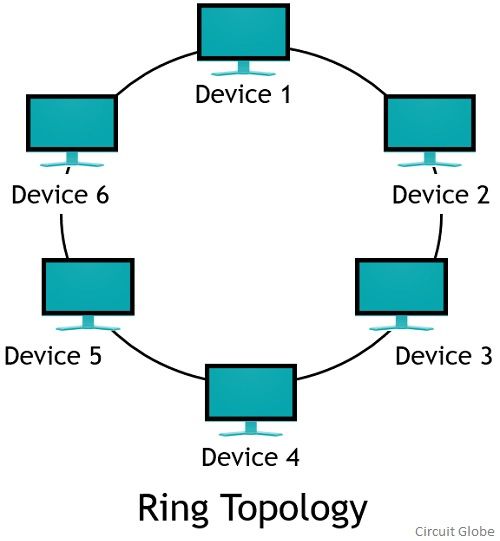
- Ring Topology: In a ring topology, devices are connected in a closed loop or ring. Each device is connected to two other devices, creating a continuous circular path for data transmission. The advantage of this topology is that data travels in only one direction, improving efficiency. However, if one device or connection fails, it can disrupt the entire network.
Mesh Topology: In a mesh topology, each device is connected to every other device in the network, forming a fully interconnected structure. This type of topology provides redundant paths for data transmission, increasing fault tolerance and reliability. However, the high number of connections can make it expensive and complex to implement.
Tree Topology: Also known as a hierarchical topology, the tree topology resembles a hierarchical structure, with devices organized into levels or layers. It combines multiple star topologies connected to a central bus or backbone. This topology allows for scalability and ease of management. However, if the central backbone fails, it can disrupt the entire network.
Hybrid Topology: A hybrid topology combines two or more different topologies to take advantage of their strengths and mitigate their weaknesses. For example, a network may use a combination of star and mesh topologies, where multiple star networks are interconnected through mesh connections.
These are the main network topologies used in networking. The choice of topology depends on factors such as network size, cost, scalability, fault tolerance, and performance requirements.


